For many companies, business value resides in their data and network systems. A sophisticated community of cyber criminals and organized crime syndicates however are motivated to cause competitive harm and financial loss by exploiting technical and social vulnerabilities of information assets. This combination of opportunity and risk poses a higher likelihood of data breach. Realizing the significance of the threat outcome, the State of New York has taken proactive measures to guard against financial crisis and to protect consumers and markets from fraud. We will discuss one such measure in this post.
Companies in the financial sector interested in doing business in New York, USA or already doing business in the state must now comply with a recently issued cyber law. In February 2017, the New York State Department of Financial Services (NYDFS) launched the NYDFS Cybersecurity Regulation (23 NYCRR 500), which placed cybersecurity requirements on all financial institutions operating under the NYDFS licensure (currently over 3,000 organizations) and their vendors.
The purpose of this regulation is “to promote the protection of customer information as well as the information technology systems of regulated entities.” Customer information can be summed up as sensitive nonpublic information which is essentially consumer personally identifiable information (PII); data that can be used to identify an individual.
Like the GDPR, the New York regulation has rules for basic principles of data security, risk assessments, documentation of security policies, and designating a chief information security officer (CISO) to be responsible for the program.
Unlike the GDPR, the regulation has very specific data security controls, including annual pen testing and vulnerability scans! The new regulation has 23 sections that align to NIST’s Cybersecurity Framework and ISO 27001, hence reducing some of the burden on those that already have security measures in place in accordance with either of these frameworks. But for those that do not, the regulation requires organizations to develop and implement an effective cybersecurity program that covers their systems and that of their third-party vendors.
Who Does this Law Apply to?
The NYDFS Cybersecurity Regulation applies to all entities including any persons “operating under or required to operate under DFS licensure, registration, charter, certificate, permit, accreditation or similar authorization under the Banking Law, the Insurance Law or the Financial Services Law”, as well as, by extension, unregulated third-party service providers to regulated entities. Covered entities include the following:
- State-chartered banks
- Licensed lenders
- Private bankers
- Foreign banks (NY operations)
- Mortgage companies
- Insurance companies
- Service providers
Not complying with the regulation becomes a legal matter.
Who is Not Covered?
There are limited exemptions to the NYDFS Cybersecurity Regulation. Organizations that employ less than 10 people and contractors, produced less than $5 million in gross annual revenue from New York operations in each of the past three years, or hold less than $10 million in year-end total assets are exempt from certain requirements of the Regulation. All charitable and foreign risk groups operating in NY are automatically exempt from the Regulation.
Phased Timeline to Comply
The NYDFS Cybersecurity Regulation included a phased implementation process, with four distinct phases allowing organizations time to implement more robust policies and controls. The graphic below summarizes each of the four phases, their effective date and a few specific requirements.
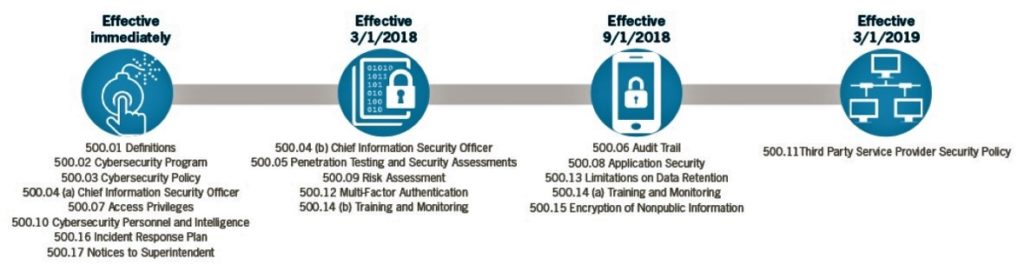
Phase 1 required the implementation of basic security, including robust cybersecurity policies and designating a CISO who reports in writing to the board of directors annually.
Phase 2 established reporting procedures whereby the CISO prepares an annual report that covers cyber risks and effectiveness of existing measures. This phase also required the implementation of a cyber security program that continuously evaluates risks and the performance of an initial risk assessment.
Phase 3 is for developing the cyber program. Here organizations institute a comprehensive cybersecurity program, implement encryption, penetration testing and other robust security control measures.
Phase 4 is dedicated to securing third parties. Organizations develop policies to identify and perform risk assessment of third-party vendors who have access to their systems and files. Also, organizations evaluate the effectiveness of their third-party vendor’s security practices periodically.
Key Requirements of the Regulation
Organizations must use qualified, continuously trained cybersecurity personnel to manage evolving threats and responses, must notify NYDFS about all cyber events that carry a ‘reasonable likelihood’ of causing material harm (but any events that harm consumer MUST be reported), and must limit and monitor access privileges granted to users.
Covered entities will have to implement the following:
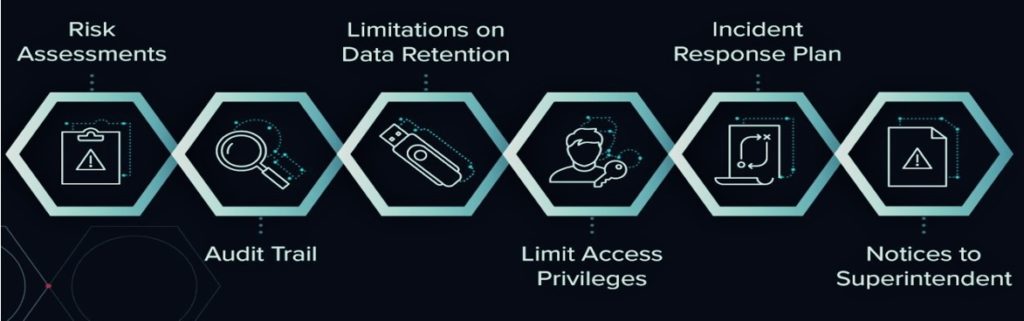
- Risk Assessments – Performed periodically and will be used to assess “confidentiality, integrity, security and availability of the IT infrastructure and PII. (Section 500.09)
- Audit Trail – Designed to record and respond to cybersecurity events. The records will have to be maintained for five years. (Section 500.06)
- Limitations on Data Retention – Develop policies and procedures for the “secure disposal” of PII that is “no longer necessary for business operations or for other legitimate business purposes” (Section 500.13)
- Access Privileges – Limit access privileges to PII and periodically review those privileges. (Section 500.07)
- Incident Response Plan – Develop a written plan to document internal processes for responding to cybersecurity events, including communication plans, roles and responsibilities, and necessary remediations of controls as needed. (Section 500.16)
- Notices to Superintendent – Notifications to the NYFS within at most 72-hours after a “material” cybersecurity event has been detected. (Section 500.17)
Moreover, organizations will need to implement data encryption, enhanced multi-factor authentication, and submit an annual certification to confirm their compliance with all aspects of the regulations.
Penalties and Consequences
Violations can incur fines of $250,000 or one percent of total banking assets, injunctive relief (e.g., possible revocation of a license), and orders requiring corrective action.
Vendor Self-Certification
Can you rely upon your third-party vendor’s self-certification? The short answer is, no. NYSDFS emphasizes the importance of a thorough due diligence process in evaluating your vendors. Solely relying on their certification is not due-diligence. Covered entities must assess the risks from their vendor and extend the review to their data, systems and effectiveness in addressing those risks.
How ControlPoints Can Help
According to Verizon’s 2017 Data Breach Investigation Report, nearly 50% of financial industry-related incidents result in a data breach. The vast majority of the threat actors are external and are motivated by financial gain.
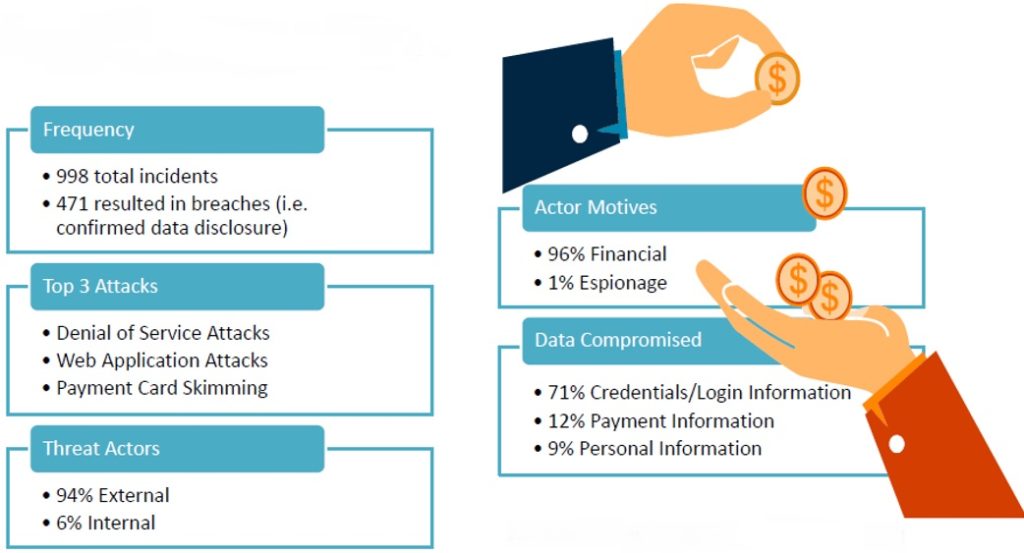
The findings above impress upon the clearly defined goals of the regulation – to protect sensitive information and IT systems, take a risk-based approach to cybersecurity, and institute accountability for cybersecurity by the C-Suite and Board.
ControlPoints can help you make sense of the regulation, steer your implementation in the right direction and verify your third-party vendor’s control environment satisfy all requirements. Implement your cybersecurity program designed to effectively detect threats, prevent breaches and adequately respond to attacks, such as denial-of-service (DoS) and ransomware. Complete an effective risk assessment to flag excessive permissions, establish unified audit trails, and lock down sensitive PII. Give your cyber staff professional training from a cybersecurity leader to ensure effective management of risks across the enterprise.