Data Privacy: Navigating the Complexities of Global Regulations
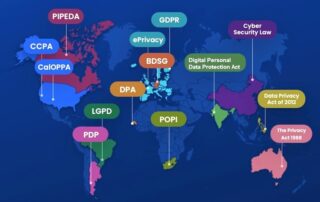
In today’s digital landscape, organizations must navigate an intricate web of global data privacy regulations, such as GDPR and CCPA, to protect personal information. GRC professionals play a crucial role in ensuring compliance while managing the complexities of diverse legal requirements and emerging privacy laws.