Proprietary data, expert analysis and bold thinking for leaders who want to achieve the extraordinary.
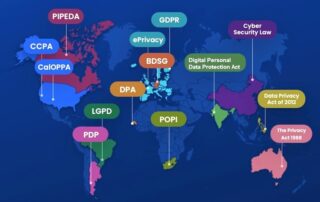
Data Privacy: Navigating the Complexities of Global Regulations
In today’s digital landscape, organizations must navigate an intricate web of global data privacy regulations, such as GDPR and CCPA, to protect personal information. GRC professionals play a crucial role in ensuring compliance while managing the complexities of diverse legal requirements and emerging privacy laws.
How Email Security Gaps Led to a $1.5 Million Bank Fraud
Discover how a sophisticated email compromise led to a staggering $1.5 million theft, revealing critical vulnerabilities in cybersecurity. Learn essential strategies to fortify defenses and protect against the ever-evolving landscape of cyber threats.
Unique Aspects of GRC Cybersecurity in IT/OT Manufacturing
Manufacturing faces unique GRC cybersecurity challenges due to the convergence of IT and OT, complex global supply chains, and stringent regulatory requirements. Understanding these complexities is crucial for developing robust strategies that safeguard operations, intellectual property, and compliance.
Why Continuous Monitoring is Your Best Defense Against Evolving Cyber Threats
Continuous monitoring is crucial for maintaining a robust security posture amidst a dynamic cyber threat landscape. By integrating real-time vigilance and leveraging advanced tools, organizations can swiftly detect and respond to emerging threats while ensuring compliance with regulatory requirements.
Integrating HIPAA and NIST for Enhanced Healthcare Cybersecurity
Integrating HIPAA and NIST frameworks is vital for robust cybersecurity in digital healthcare, ensuring regulatory compliance and a strong security posture. A well-established GRC department enhances this integration by supporting proactive risk management and continuous improvement.
The Gambia’s Central Bank Hack: The Need for NIST CSF and RMF
The recent cyberattack on The Gambia's Central Bank highlights the critical vulnerability of infrastructure to cyber threats, with hackers potentially stealing two terabytes of sensitive data. The incident underscores the urgent need for robust cybersecurity measures to protect against sophisticated attacks and safeguard personal information.
The Evolution of Cyber Threats in Healthcare: Past, Present, and Future
The evolution of cyber threats in healthcare highlights the urgent need for robust cybersecurity measures to protect patient data and ensure service continuity. Embracing advanced technologies while addressing cyber risks is essential for maintaining trust and integrity in healthcare.
SolarWinds Orion Countermeasures
The sophistication and audacious scale of the SolarWinds Orion attack is an inflection point for governments, organizations and security defenders worldwide. This post identifies the root causes and recommends unique technical and regulatory improvements.
Guide to CMMC Certification
CMMC was established to ensure greater cyber consistency from defense contractors and will be an absolute requirement to win DoD RFPs and/or have a contract awarded. Accelerate your readiness with our detailed guide.
5 Best Free VPNs in 2021
Is your VPN spying on you? Most VPNs fail to live up to their promise not to. With thousands to choose from, read our report to find out the 5 Best FREE VPNs the pros use that offer real anonymity on the world wide web, grant access to blocked content and secure all of your communication.