In these uncertain times, the Department of Defense (DoD) continues moving forward with its plans for the Cybersecurity Maturity Model Certification (CMMC). Though the onset of COVID-19 has somewhat slowed assessment program efforts and the subsequent training involved, the goal to protect highly sensitive information remains intact. Continuous probing by Nation-State actors, routine occurrences of ransomware attacks and the recent SUNBURST malware campaign reinforce the fact supply chain vulnerabilities remain a preferred attack vector of cyber criminals. With the program recently taking flight, defense organizations in the DoD supply chain exploring the level of support required for their CMMC requirements will find helpful background and actionable tips in this post.
What is CMMC?
CMMC stands for “Cybersecurity Maturity Model Certification” and is a unifying standard for the implementation of cybersecurity across the Defense Industrial Base (DIB). The CMMC framework includes a comprehensive and scalable certification element to verify the implementation of processes and practices associated with the achievement of a cybersecurity maturity level. The DoD designed CMMC to provide increased assurance that a DIB company can adequately protect sensitive unclassified information, accounting for information flow down to subcontractors in a multi-tier supply chain.
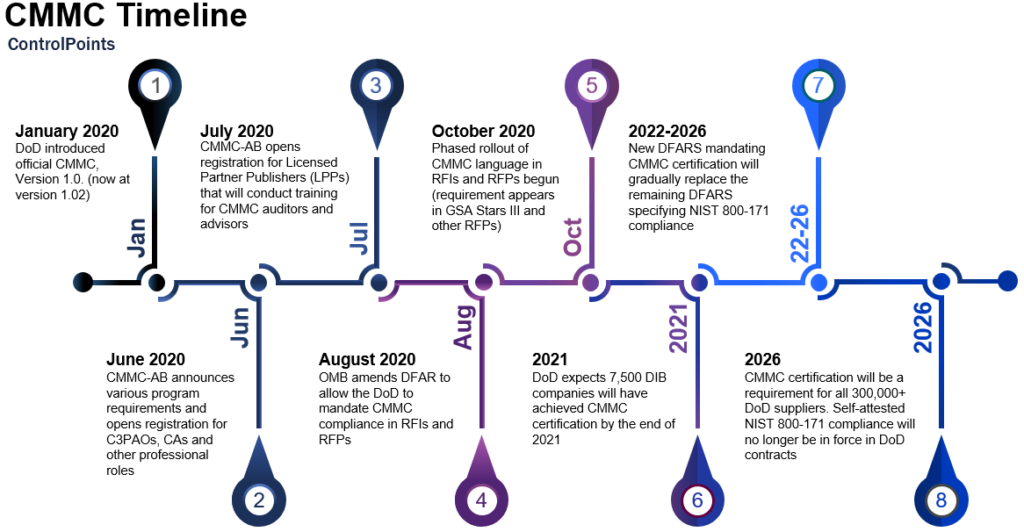
The official CMMC model was released January 2020 and beginning October 2020 language appeared in requests for information (RFI) and requests for proposal (RFP) bids requiring all organizations receiving DoD funding to address CMMC requirements.
Previously, the DIB’s compliance to the various cybersecurity standards and best practices were largely self-certified. CMMC introduces the requirement for a certified third-party assessment organization (3PAO) to review systems and processes for the purpose of issuing certification. To standardize this process, the DoD established a non-profit, independent organization, the CMMC Accreditation Body (CMMC-AB), to define the assessment and administration needed for certification.
The CMMC-AB also offers assessors to evaluate the cybersecurity posture of DoD contractors. The audit process is intended to verify that a company’s security controls, policies and procedures comply with their CMMC mandate level prior to award and throughout the life of a contract. Once an organization obtains an approved certification, it is will be valid for three years.
Technical Details
The CMMC was developed in collaboration with university research centers, federally funded R&D centers and industry experts. It unifies several existing security standards into one comprehensive framework, including NIST SP 800-171, NIST SP 800-53, ISO 27001, ISO 27032, FISMA and AIA NAS9933 – and constructed with existing regulations, such as Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012. There is also some overlap with Supply Chain Risk Management (SRCM) and the Capability Maturity Model Integration (CMMI).
CMMC is developed for the protection of FCI and CUI data:
- Federal Contract Information (FCI) – This is information not intended for public release. This information is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government. FCI does not include information provided by the Government to the public (such as public websites or simple transactional information necessary to process payments). Source: 48 CFR 52.204.21
- Controlled Unclassified Information (CUI) – This is information that requires safeguarding or dissemination controls, pursuant to and consistent with the law, regulation, or government-wide policy. This includes information the government creates or possesses, or that an entity creates or possesses for or on behalf of the government. Source: E.O. 13556 (adapted)
Additional types of CUI data include:
- Controlled Technical Information (CTI) – Technical information with military or space application that is subject to controls on its access, use, reproduction, modification, performance, display, release, disclosure or dissemination.
- Covered Defense Information (CDI) – Defined in DFARS 252.204-7012 as unclassified CTI or other information, as described in the CUI registry that requires safeguarding or dissemination controls pursuant to and consistent with law, regulations and government-wide policies.
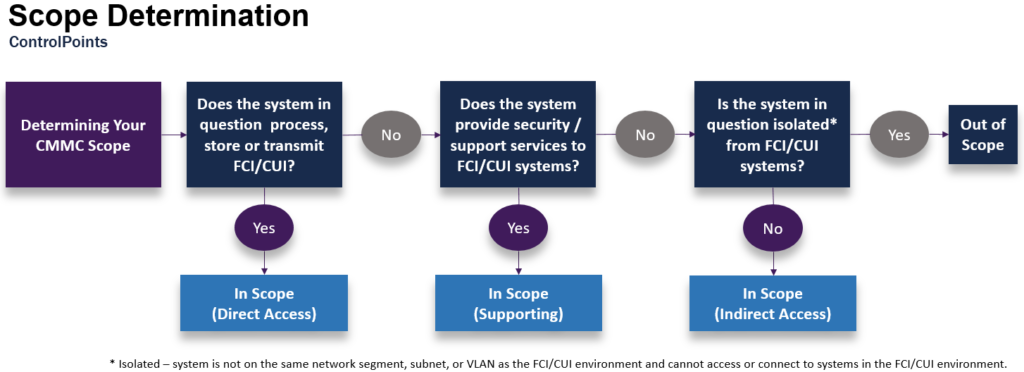
In short, FCI and CUI is any information that an adversary should not see. The following decision diagram can help your organization determine the scope of systems, if any, which support FCI and CUI data.
CMMC Control Domains
The CMMC model includes 17 capability or control domains. Many of the control domains are derived from NIST 800-171 and the associated security areas in Federal Information Processing Standards (FIPS) Publication 200, plus three additional domains (Asset Management, Recovery and Situational Awareness). A brief explanation of each follows.
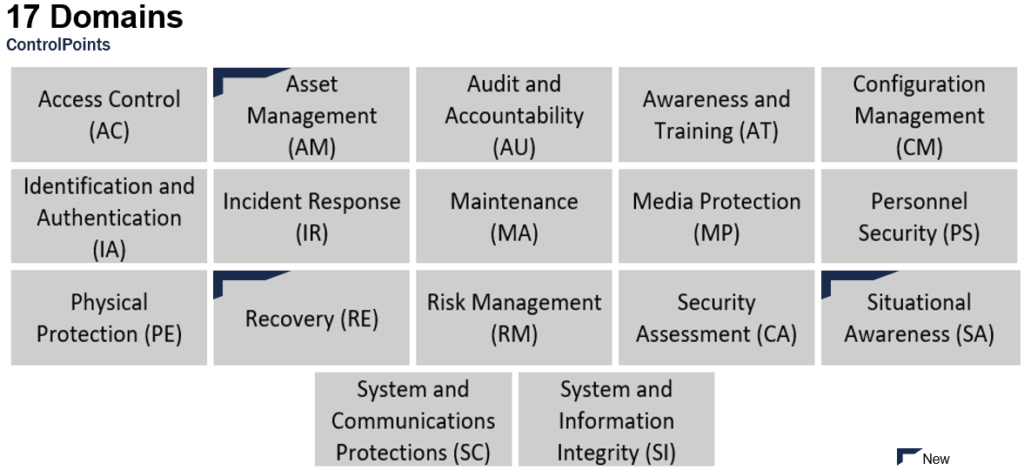
- Access Control—Who has access to your systems (including remote access) and what are their roles and permissions?
- Asset Management—Can you locate, identify and inventory your assets?
- Audit and Accountability—Can you track the users who have access to your CUI, so they are accountable for their actions?
- Awareness and Training—Do all staff have security awareness training?
- Configuration Management—Do you have configuration baselines for your systems so you can gauge their effectiveness?
- Identification and Authentication—Does your organization have properly defined roles with appropriate data access levels, including processes for reporting and accountability?
- Incident response—Do you have an Incident Response Plan that documents how you will detect, report and respond to incidents, including post incident analysis?
- Maintenance—Do you have procedures in place to maintain and operate your cyber controls?
- Media Protection—Is your media identified and marked for quick access, and do you have media protection, transportation and disposal protocols in place?
- Personnel Security—Have staff been properly screened, and do you have controls in place to protect CUI during staff turnover?
- Physical Protection—Do you have provably adequate physical security protecting your assets?
- Recovery—Do you have a robust, tested process for making and logging backups to protect your sensitive data from data loss and damage?
- Risk Management—Do you have a process to periodically identify and assess risks to your FCI and/or CUI, including vendor-related risks?
- Security Assessment—Do you have a system security plan in place?
- Situational Awareness—Do you have a threat monitoring system in place?
- System and Communications Protection—Do you have verifiable control of communications at system boundaries?
- Systems and Information Integrity—Can you effectively monitor your environment to identify and mitigate vulnerabilities and flaws?
CMMC Model
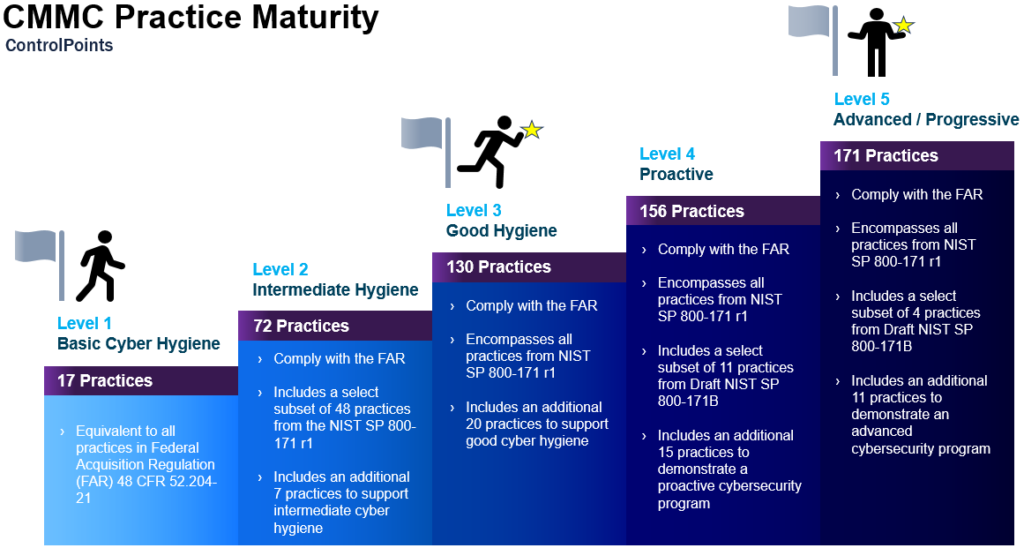
The CMMC model defines five Levels to measure maturity (via Processes) and technical capability (via Practices) utilizing the 17 control domains.
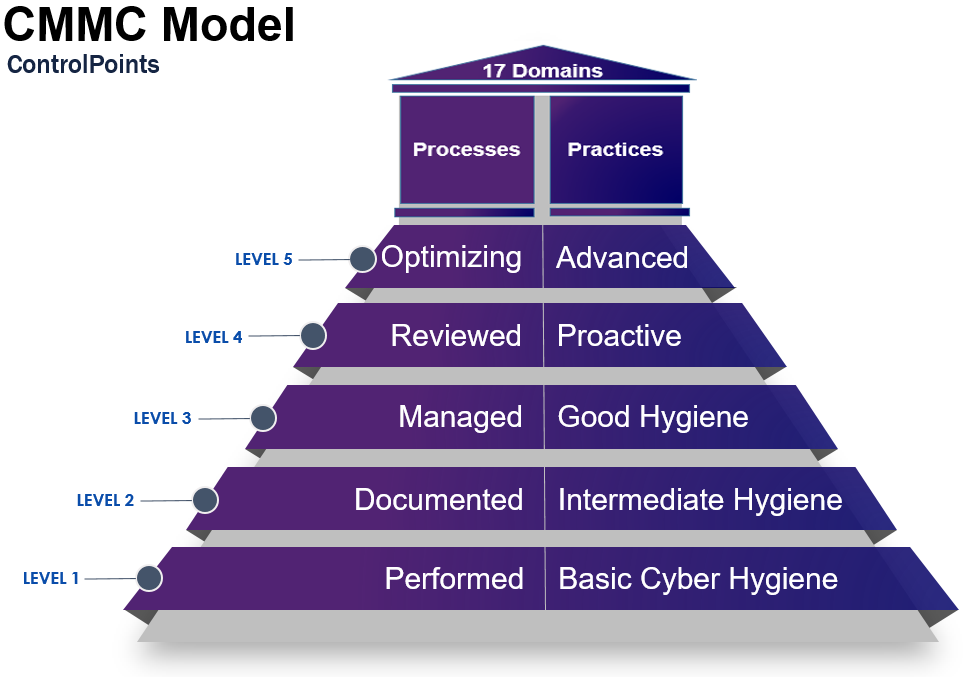
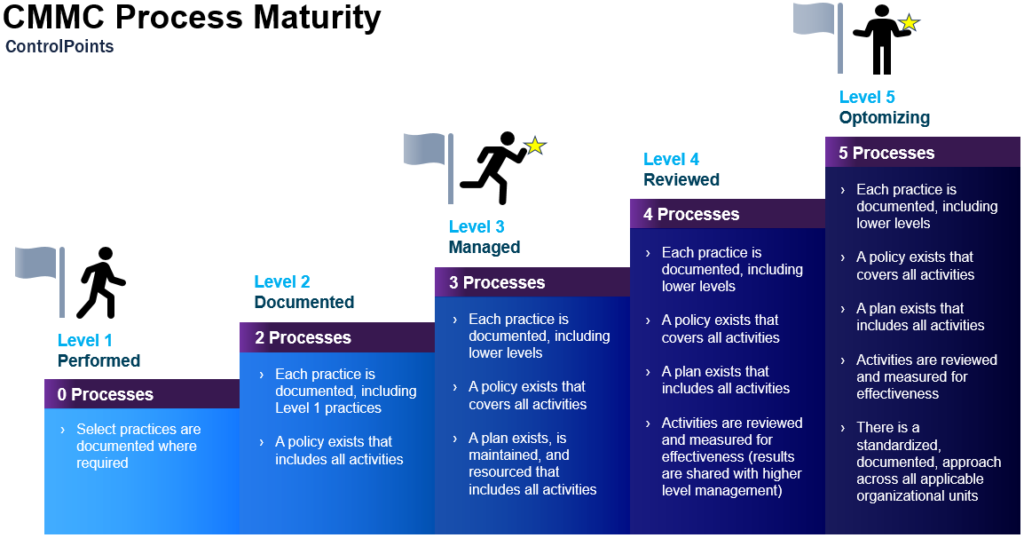
Level 1 is where the DoD expects most firms to be currently. Level 2 is meant to be a stepping-stone to Level 3, where firms get into the practice of documenting each Practice involving CUI. Level 3 is a managed state where a policy has been put into place and maintained to cover all activities and fully documented CUI Practices. Level 4 is a higher level of cybersecurity for limited incidences of highly sensitive information, where activities are reviewed and measured for effectiveness. Level 5 is the optimized zone, with a standardized, documented, and tested approach seen across all applicable organizational units. Let us get into the specifics of each Level:
Level 1– Basic Cyber Hygiene, includes 0 Processes and 17 Practices as specified in 48 CFR 52.24-21, Basic Safeguarding of Covered Contractor Information Systems. It focuses on protecting FCI. To be certified at this level, a supplier only needs to demonstrate that it can perform the required practices in an ad hoc manner, potentially without accompanying documentation.
Level 2– Intermediate Cyber Hygiene, introduces 2 Processes and 55 additional Practices (e.g., implement 55 controls required to protect CUI at Level 3). At Level 2, processes must be documented and should be practiced accordingly.
Level 3– Good Cyber Hygiene, includes an additional Process and 58 additional Practices. Focuses on protecting CUI. It includes all 110 controls specified in NIST 800-171 plus 20 additional controls (i.e., combined 130 controls). To gain CMMC Level 3 certification, a business must show that it has documented and is actively managing cybersecurity policies and processes in alignment with an established plan.
Level 4– Proactive, includes an additional Process and 26 additional Practices. At this level, firms must demonstrate that they can proactively defend CUI against advanced persistent threats (APTs) and other ongoing, sophisticated and dynamic attacks. Level 4 requires implementation of 26 additional controls beyond CMMC Level 3. It also requires companies to evaluate the effectiveness of its controls, document threats and responses on an ongoing/historical basis, and take corrective action where needed to detect and defeat threats, in coordination with management. Note: There are no assessors yet that can perform a Level 4 certification.
Level 5– Advanced/Progressive, includes an additional Process and 15 additional Practices. This level focuses on protecting CUI from multi-vector, state-of-the-art APTs mounted by government-sponsored hackers. It requires the demonstrable ability to audit, optimize and standardize cybersecurity controls and processes. Demanding a robust security posture, this will be a challenging level for many SMBs to meet with in-house staff and expertise. Note: There are no assessors yet that can perform a Level 5 certification.
Why is CMMC Necessary Given 800-171?
CMMC was established to ensure greater cyber consistency from defense contractors. The DoD realized NIST SP 800-171 requirements were often widely interpreted and companies could extend Plans of Action and Milestones (POA&M) to cover gaps indefinitely. Through various auditing mechanisms it was also becoming apparent contractors were simply not compliant with NIST SP 800-171. “DoD contractors did not consistently implement DoD-mandated system security controls for safeguarding Defense information.” (via DoD OIG Report finding, July 2019). Moreover, Congress continues to raise concerns around cyber and supply chain that impact the DoD’s mission. CMMC alleviates these pressures by enabling a trust but verify mechanism via a formalized third-party certification.
Why is CMMC Necessary Given DFARS 252.204-7012?
Under the original DFARS 252.204-7012 clause that has been in force in DoD contracts since December 2017, many (if not most) suppliers are simply self-attesting to DFARS compliance without materially bringing their systems and processes into compliance. As previously mentioned, this has resulted in uneven security among critical suppliers.
In November 2020, the DoD passed Defense Federal Acquisition Regulation Supplement 252.204-7019 (DFARS 7019) in order to standardize cybersecurity across the DIB. DFARS 7019 is one of three interrelated clauses that the DoD’s new interim rule adds to the DFARS (the others being 7020 and 7021). Related FAR and DFARS Clauses:
- FAR 52.204-21: Basic Safeguarding of Covered Contractor Information Systems [Limitations: only covers information systems, not the information contained in those systems. Contains no requirements for training, penetration testing, cyber incident reporting, or cyber insurance. This is equivalent to CMMC Level 1]
- DFARS 252.204.7012: Safeguarding Covered Defense Information and Cyber Incident Reporting [Covers information and information systems. Incorporates NIST 800-171. Requires implementation of 110 security requirements in SSP and POA&Ms. Requires “rapid report” of cyber incidents within “72 hours of discovery”.]
- DFARS clause 252.204-7019: Notice of NIST SP 800-171 DoD Assessment Requirements
- DFARS clause 252.204-7020: NIST SP 800-171 DoD Assessment Requirements
- DFARS clause 252.204-7021: Cybersecurity Maturity Model Certification Requirements [Formally establishes CMMC AB and C3PAOs. Requires Contractors to maintain the requisite CMMC level for the duration of the contract and flow down same requirements to subcontractors in “all subcontracts and other contractual instruments.”
The DFARS 7019 clause describes the requirements that contractors must meet to correctly report and maintain their self-assessments concerning compliance with the NIST 800-171 cybersecurity framework under DFARS 7012. DFARS 7019 also specifies the requirements for contracting officers to make or deny contract awards based on a supplier’s reported assessment results (posted in SPRS – the Supplier Performance Risk System).
In other words, the DFARS 7019 clause puts DIB suppliers on notice that they are required to assess and report their own NIST 800-171 compliance in the form of an SPRS score less than three years old (or newer if required). Firms that have a current SPRS Basic, Medium, or High assessment on file, and follow the NIST SP 800-171 DoD Assessment Methodology, along with an up-to-date System Security Plan (SSP) and a POA&M, if required, will likely meet the DFARS 7019 clause requirements. However, given the inherent flaw in self-attestation (the lack of independence), the DOD and other government agencies now mandate a higher level of attestation through the Cybersecurity Maturity Model Certification (CMMC).
Key milestones on the CMMC timeline
Who Must Achieve CMMC Certification?
Until October 1, 2025, CMMC requirements will only be included in new acquisitions. Organizations—prime contractor or subcontractor—that participate in DoD contracts in the interim will need to achieve some level of CMMC certification within the next few years. Even companies that provide nontechnical services like construction or custodial services will need to demonstrate “basic cyber hygiene” (CMMC Level 1).
Businesses that handle CUI will need to be certified to at least CMMC Level 3, which roughly corresponds to the “security maturity” already mandated by DFARS. Those that handle FCI but not CUI will need CMMC Level 1 certification. Companies that “solely produce Commercial-Off-The-Shelf (COTS) products” purchased as part of a DoD contract do not require a CMMC certification, according to the DoD.
To become certified, a supplier will need to implement their CMMC program then choose a C3PAO to schedule an assessment. The C3PAO will provide a Control Assessor (CA) who will identify vulnerabilities and gaps in relation to the requirements at the supplier’s specific level. Depending on the severity of findings, the supplier may need to rectify issues before being certified or establish POA&Ms to formally manage risk.
A supplier’s successful achievement of a CMMC certification at a particular level will be a matter of public record. Other information specific to audits, including failed certification efforts and audit findings, will not be made public.
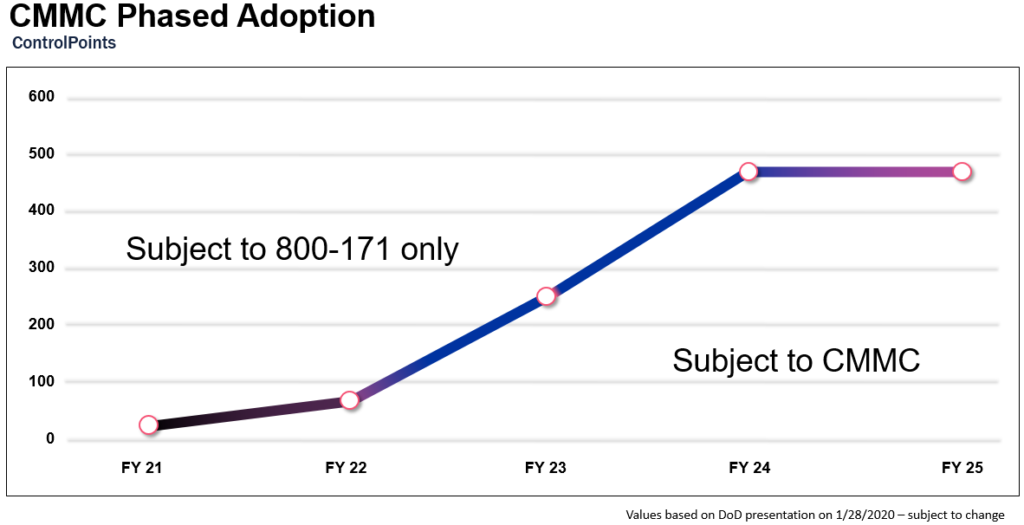
The DoD forecasts 50-70% of contractors will only require Level 1. Level 3 certification indicates a supplier is handling CUI. Suppliers that have FedRAMP authorization will likely reciprocate to a CMMC Level 3, but this depends on various factors (e.g., additional systems that may be in CMMC’s scope).
The DoD expects a phased adoption rate. 100% of suppliers handling FCI and CUI will need to comply with CMMC requirements by FY 26 (with the exception of COTS procurement). Between FY 21 and FY 25, suppliers handling CUI will have the burden of proof to comply with CMMC.
Preparing for CMMC
CMMC certification will be an absolute requirement to win DoD RFPs and/or have a contract awarded. Many contractors, especially SMBs with limited resources, have been challenged to comprehend the NIST 800-171 requirements, let alone implement them. Others have either outsourced their compliance programs or employed significant expertise to sustain compliance in-house.
Currently, the CMMC-AB is in the process of licensing assessors and the firms that will serve as 3PAOs.
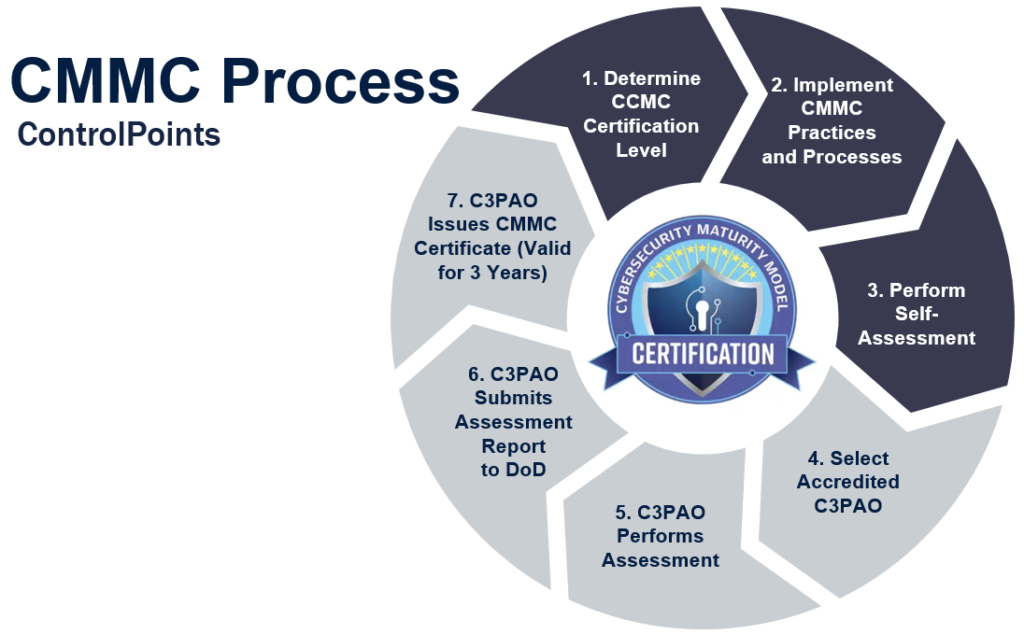
However, a 3PAO organization is not needed to prepare for the certification, in fact a 3PAO creates a conflict of interest if providing Steps 1-3 and also Steps 4-7. This is expressly prohibited by the CMMC AB. An experienced firm can help organizations design, document and implement the necessary security measures (Steps 1-3) in preparation to obtain 3PAO certification. This approach can save time and cost of locating a limited supply of 3PAOs simply to prepare for the certification, especially when one is not even necessary to simply implement the requirements.
Organizations can accelerate their CMMC adoption by leveraging our CMMC readiness planning, gap assessment, high quality templates, control implementation, and honed processes to reduce the compliance lift and with less cost. Our simple 4-step turn-key process gets you to CMMC Level 1 and Level 3 quickly.
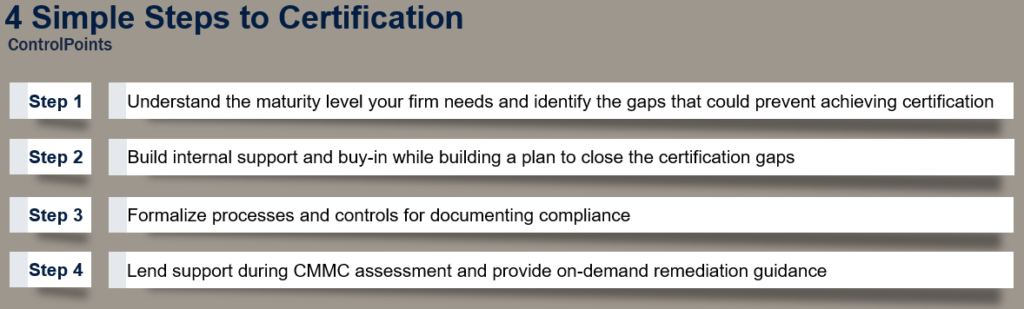
We have deep experience with implementing NIST SP 800-171 controls that support DFARS 252.204-7012 and 7019, adapted to form the basis of the CMMC framework.
Are you ready to accurately define your CMMC pathway, take flight from the runway and go forward with certainty? We can help you get there faster.





